Cpu on board with cyber attack hologram. Cyber attack hologram over working cpu in background. danger alert, threat, | CanStock
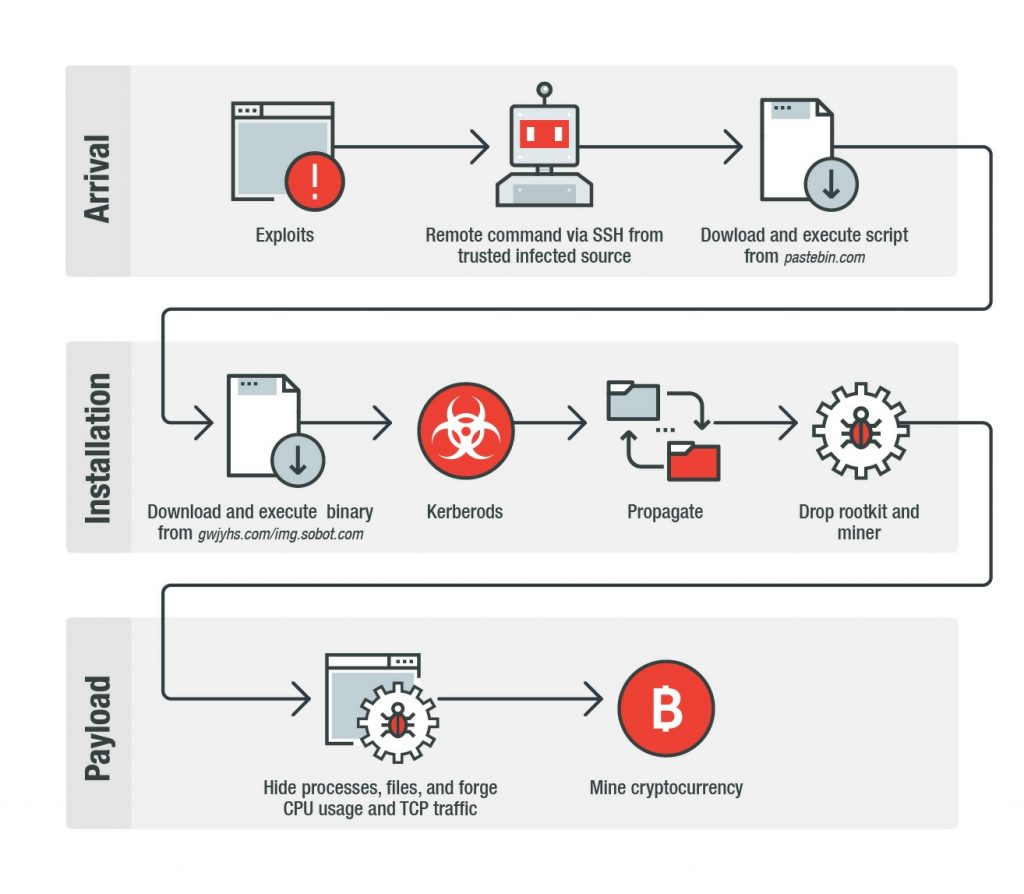
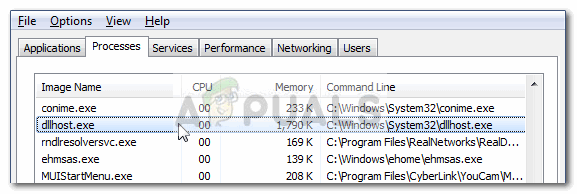
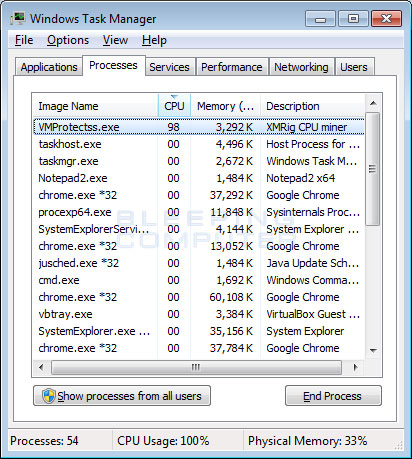
GitHub - Menziess/smbd-cpuminer-infection-fix: A Samba exploit turned Linux into a goldmine. Those infected by the malware would have their systems mining cryptocurrency 24/7, causing their cpu to maintain a 100% usage. My
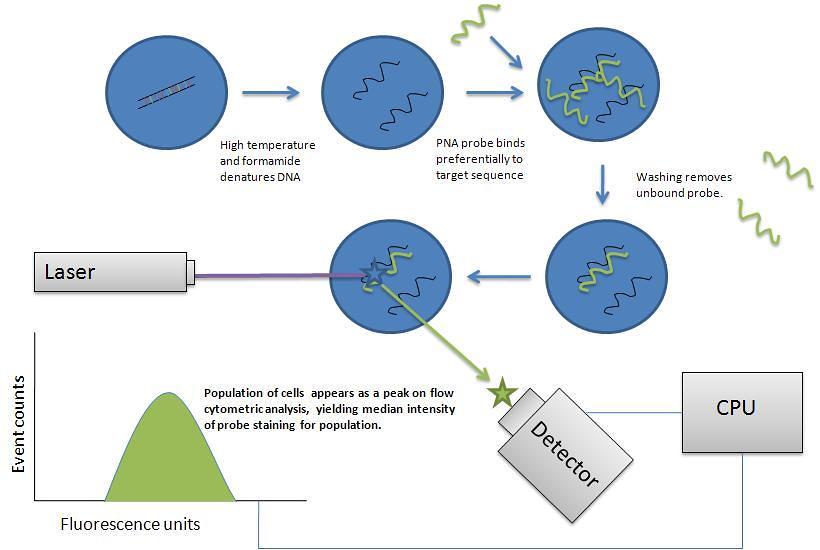
Peripheral blood cell-specific cytokines in persons with untreated HIV infection in Malawi, Africa | Jason and Jarvis Associates, LLC

Cpu On Board With Cyber Attack And Skull Hologram Stock Photo - Download Image Now - Blue, CPU, Computer - iStock

Cyber attack and skull glowing hologram over working cpu in background. Danger alert, threat, infection and warning abstract concept with skull symbol Stock Photo - Alamy

CPU Virus Infection Spreading Across the Motherboard Stock Illustration - Illustration of connecting, power: 134355324

Pichia-secreted mVHH-IgA prevents F4-ETEC infection in piglets a,b,... | Download Scientific Diagram

Cyber attack and skull glowing hologram over working cpu in background. Danger alert, threat, infection and warning abstract concept with skull symbol Stock Photo - Alamy

PDF) Usefulness and problems of the urinary tract infection criteria for evaluating drug effi cacy for complicated urinary tract infections | Katsumi Shigemura - Academia.edu